If you have an AWS deployment, make sure you turn on AWS Config. It has a whole bunch of built-in rules, and you can add your own to validate the security of your AWS environment as it relates to AWS services. Amazon provides good documentation, a GitHub repo, and SumoLogic does a quick How-to turn it on. It’s straightforward to turn on and use. AWS provides some pre-configured rules, and that’s what this AWS environment will validate against. There is a screenshot below of the results. Aside from turning it on, you have to decide which rules are valid for you. For instance, not all S3 buckets have business requirements to replicate, so I’d expect this to always be a noncompliant resource.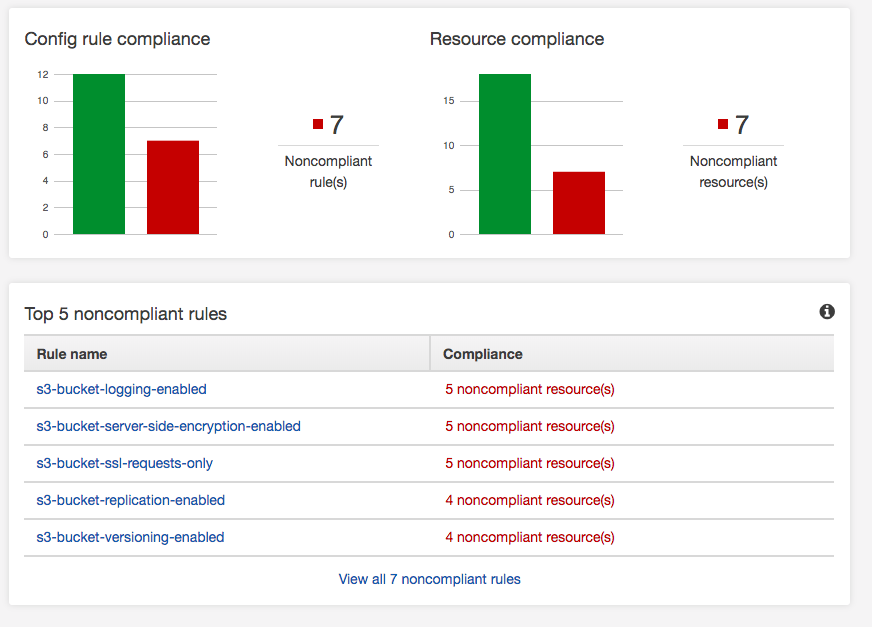 However, one of my findings yesterday was missing EBS encrypted volumes. In order to make EBS volumes encrypted its 9 easy steps:
However, one of my findings yesterday was missing EBS encrypted volumes. In order to make EBS volumes encrypted its 9 easy steps:
-
Make a snapshot of the EBS Volumes.
-
Copy the snapshot of the EBS Volume to a Snapshot, but select encryption. Use the AWS KMS key you prefer or Amazon default aws/ebs.
-
Create an AMI image from the encrypted Snapshot.
-
Launch the AMI image from the encrypted Snapshot to create a new instance.
-
Check the new instance is functioning correctly, and there are no issues.
-
Update EIPs, load balancers, DNS, etc. to point to the new instance.
-
Stop the old un-encrypted instances.
-
Delete the un-encrypted snapshots.
-
Terminate the old un-encrypted instances.
Remember KMS gives you 20,000 request per month for free, then the service is billable.
